🕶️ Shadow IT: The Silent Risk Hiding Inside Your Business
Every modern business runs on technology — but not all of that tech is visible, secured, or even approved. In fact, some of the biggest risks to your organization might not come from hackers… but from your own team’s well-intentioned workarounds.
This hidden tech stack is called Shadow IT — and if you’re not seeing it, chances are it’s already growing.
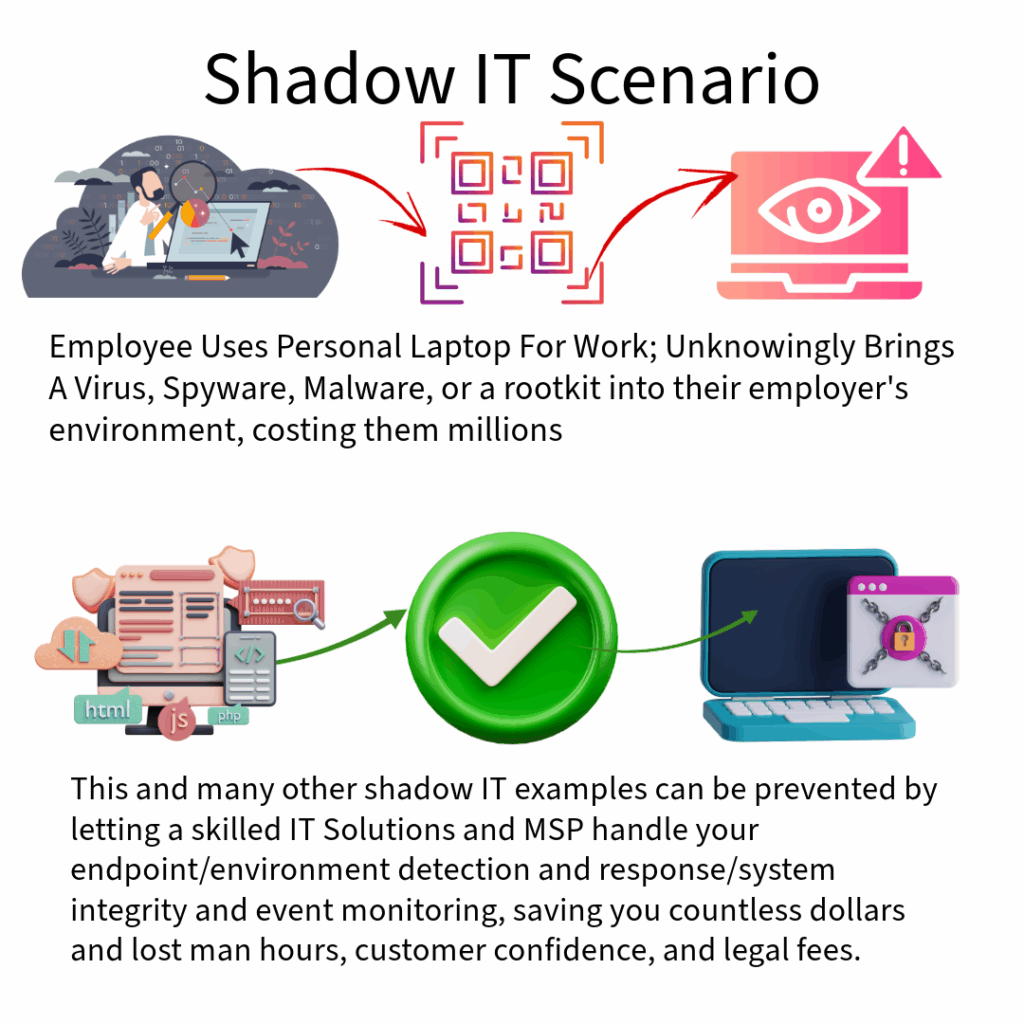
🕵️♀️ What Is Shadow IT?
Shadow IT refers to software, apps, devices, or services that employees use without the knowledge or approval of the IT team or leadership. Think:
- Employees syncing files to personal Dropbox accounts
- Using personal laptops or phones for work tasks
- Installing browser plugins or using AI tools with sensitive data
- Creating free accounts with platforms like Slack, Canva, or Zoom — but without any IT oversight
It’s not malicious. In most cases, it’s just someone trying to get their job done faster.
But unmanaged = unsecured.
🚨 Why Shadow IT Is a Problem
1. Data Leaks & Privacy Violations
Unapproved tools often bypass encryption, logging, and access control — leaving your sensitive data exposed without your knowledge.
2. Compliance Risk
If you’re required to follow HIPAA, PCI-DSS, or even local privacy laws — using unauthorized tools can put you out of compliance fast (even unknowingly).
3. Increased Attack Surface
Every app or cloud service is a potential entry point for attackers. The more invisible tools your staff uses, the harder it is to defend the perimeter.
4. No Incident Response Path
If something goes wrong on an unmanaged device or service, you may not have backups, access logs, or even knowledge of what data was impacted.
💡 The Good News: You Don’t Have to Lock Everything Down
At BTech Solutions LLC, we don’t believe in policing your team — we believe in partnering with you to:
✅ Identify and inventory Shadow IT without blame
✅ Secure high-use tools with policies, MFA, and backup integration
✅ Provide safer, better alternatives that still let your team work fast
✅ Build a culture of secure enablement, not “just say no” IT–did you know…? We can build out specific, automated rules with tools and platforms tailored specifically to your organization’s needs and budget, that will automatically prevent, kill, and quarantine dangerous or unsecure software AND hardware from operating in your environment.
🔐 We Don’t Just Secure Your Network — We Secure Your Workflow
Our approach is grounded in real-world experience and trusted frameworks, including insights gained through our co-founder’s membership in the FBI’s InfraGard program, and years of partnering with CISA, the United States Cybersecurity and Infrastructure Security Agency.
We don’t chase trends — we secure what matters.
And yes, that includes Dropbox, Google Docs, and the AI tools your staff is already using behind the scenes.
💸 Shadow IT Is Costing You More Than You Think
- Time lost to scattered data
- Money spent on redundant or risky tools
- Liability from unmonitored access
- Frustration when “tech just doesn’t work right”
We help you solve these issues quietly, professionally, and without disrupting your team.
👥 Shadow IT Isn’t a People Problem
Let us help you bring it into the light — so you can work smarter, safer, and more efficiently.
Ready to see what’s really powering your business?
Let’s talk →
Leave a Reply